In the intricate dance of global commerce, the security of the supply chain stands as a steadfast guardian against threats both seen and unseen.As the heartbeat of the interconnected economy, safeguarding the flow of goods from manufacturer to consumer is paramount. In this article, we delve into the realm of supply chain security, exploring the best practices to enhance resilience and fortify defenses in an ever-evolving landscape of risks and challenges. Join us on a journey to discover the strategies and principles that propel businesses toward a more secure and sustainable future.
Ensuring End-to-End Visibility in the Supply Chain
In the realm of enhancing supply chain security, it is indeed crucial to implement real-time tracking systems that provide visibility into the entire supply chain. Utilizing technology such as RFID tags and GPS trackers can help companies monitor the movement of goods from start to finish, ensuring that any deviations or delays are promptly addressed.
Another best practice is to establish strong partnerships with suppliers and logistics providers. By fostering collaborative relationships and sharing data transparently,companies can enhance dialog and responsiveness,ultimately bolstering supply chain security. Additionally, conducting regular security audits and risk assessments can help identify vulnerabilities and proactively mitigate potential threats.
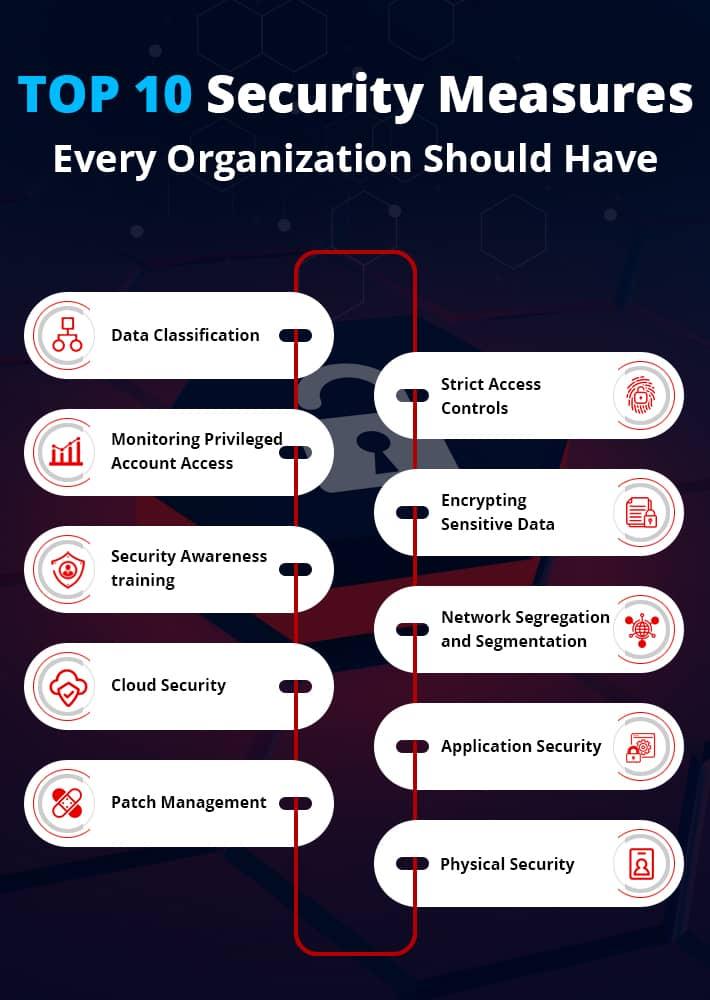
Implementing Robust Cybersecurity Measures
Implementing robust cybersecurity measures in the supply chain is crucial to protect against evolving threats and vulnerabilities. To enhance supply chain security,organizations should adopt a multi-layered approach that encompasses both technology and processes. This includes:
- Implementing end-to-end encryption to secure data in transit and at rest.
- Utilizing privileged access management to restrict access to critical systems and data.
- conducting regular security audits to identify and address potential vulnerabilities.
Moreover, fostering a culture of cybersecurity awareness among employees is essential. Providing regular training on best practices and potential threats can help mitigate risks associated with human error. By adopting these measures, organizations can bolster their cyber resilience and safeguard their supply chain against cyber threats.

Leveraging Blockchain Technology for Traceability
Blockchain technology offers unparalleled opportunities for enhancing traceability within the supply chain. By leveraging blockchain, companies can achieve greater transparency, security, and efficiency in tracking products from origin to destination. This revolutionary technology enables the creation of an immutable ledger that records each transaction,ensuring data integrity and authenticity throughout the supply chain process.
Implementing blockchain for traceability requires careful consideration of best practices to maximize its benefits.Some key strategies include:
- Utilizing Smart Contracts: Automate agreements and transactions to streamline processes and reduce risks.
- Collaborating with Partners: Establish a network of trusted partners to ensure interoperability and data sharing.
- Regular Auditing and Monitoring: Conduct frequent audits and monitor activities to detect and prevent potential security breaches.
Engaging in Proactive Risk Assessment and Mitigation
In the realm of enhancing supply chain security, is paramount. By implementing a thorough approach to identifying potential risks and taking preemptive measures to address them, companies can safeguard their supply chains against various threats and vulnerabilities.
Some best practices to consider include:
- Regular Vulnerability Scans: Conduct routine assessments to identify weak points in the supply chain infrastructure.
- Supplier Verification: Verify the credibility and security measures of all suppliers and partners.
- Incident Response Plan: Develop a detailed plan to respond swiftly and effectively in the event of a security breach.
- Employee Training: Educate employees on security protocols and best practices to mitigate risks.
Insights and Conclusions
As we navigate the ever-evolving landscape of supply chain security, it is imperative to adopt best practices that can safeguard our businesses and customers.By implementing robust strategies, leveraging cutting-edge technologies, and fostering strong partnerships, we can fortify our supply chains against potential threats and ensure seamless operations. Remember, in today’s interconnected world, vigilance and preparedness are key to maintaining the integrity and security of our supply chains. Let us continue to innovate, collaborate, and adapt to stay ahead in the pursuit of supply chain resilience.












